Penetration Testing
Friendly cyberattacks exist! Hire hackers to test your security.
What Is a Penetration Testing
Penetration Testing is a practice of testing a computer system, network or a web application to find flaws and potential security vulnerabilities. The testing is usually done by a third party in the form of a "friendly cyberattack". You can basically hire hackers to test your security. They should report honest and transparent feedback with suggestions for improvement. Their output is a part of the project documentation. Penetration Tests (or pen tests) are mandatory for certain subjects, such as banks, credit card companies, hospitals, or military organizations.
Penetration Testing requires experienced network security professionals with in-depth knowledge of computer operating systems. It is quite expensive to perform such tests, for some companies even unaffordable. If you cannot hire a third party to do the tests manually, there are always automated Penetration Test tools. Some of them even free of charge, such as OWASP, Nmap, John the Ripper, or Burp Suite. The most common approach is a combination of both manual and automated processes.
Why You Might Want the Penetration Testing
Penetration Testing helps you to:
- avoid financial damage
- improve security
- ensure that implemented controls are effective
- uncover hidden system vulnerabilities before the criminals do
- maintain the company's image and the customers' trust
- protect you and your customers
- secure user data
- follow regulations and certifications you might need
Problems the Penetration Testing Solve
- Poor code quality
- Increased cost
- Demotivated team
- Meaningless work
- Unhappy clients
How to Implement the Penetration Testing
Penetration Testing should be a part of your software development lifecycle, not after the product is developed. Fixing the issues at the end is much more expensive than dealing with them during development. Penetration Testing should be performed after every bigger code change.
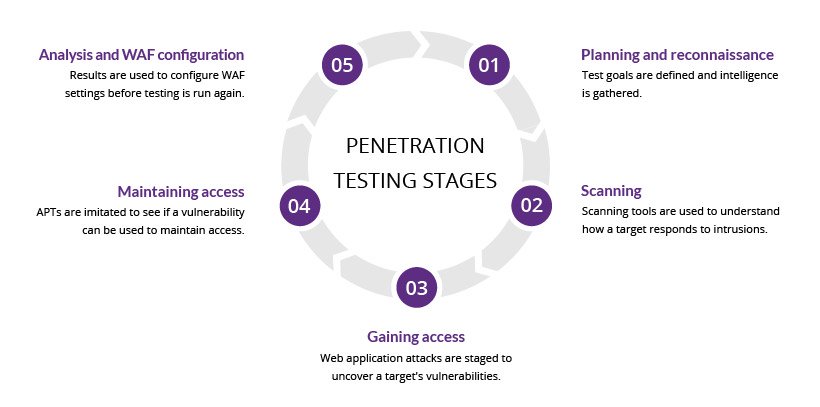
Penetration Testing involves these stages:
- Planning and reconnaissance Penetration Testers define the goals of the test and find proper testing methods.
- Scanning Testers analyze how the system responds to the test.
- Gaining access Attack the system! Testers try to break into the system with a strategy like SQL injection, backdoors, or cross-site scripting to uncover weaknesses.
- Maintaining exploit How long can the tester stay in the system? Is it long enough that the actual hacker could gain deeper access?
- Analysis and configuration review Testers make a detailed report on the performed test.
 Source: imperva: Penetration Testing
Source: imperva: Penetration Testing
Common Pitfalls of the Penetration Testing
There are potential risks involved with third-party Penetration Testing. Sensitive data can be exploited, servers can crash, systems can be corrupted. It is necessary to hire only credentialed professionals.
If you want to do the Penetration Tests by yourself, you have to train professionals. If the tests are made by unskilled programmers, it can lead to poor performance or even a system crash. In the end, it might save you some money to hire an expensive professional.
Resources for the Penetration Testing
- Tech Target: pen test (Penetration Testing)
- Cipher: The Types of Pentests You Must Know About
- IT Governance: Why is Penetration Testing necessary?
- Cybrary: 7 Best Cyber Security Penetration Testing Tools
- comparitech.com Burp Suite Cheat Sheet
Was the article helpful?
Want to write for DXKB?
Feel free to contribute. People from DXKB community will be more than happy.
Prokop Simek
CEO
Related articles
ALL ARTICLES
Proper Bug Reporting
Proper bug reporting is a crucial practice for development. It helps to understand where the product lacks its functionality or performance. Bug reports are descriptions of bugs found by testers.
Read moreSmoke Testing
It is a test aimed to verify that the most important features of the product really work. This term was used during testing hardware and the product passed the test when it did not burn or smoke.
Read morePilot Project
A Pilot Project is a small-scale version of your larger project that helps you catch potential errors before the full implementation.
Read moreCode Coverage
Code Coverage measures the percentage of source code lines that are covered by automated tests. If you have 90% CC, it means that 10% of the source code is not being tested at the moment.
Read moreClickable Prototype
Clickable Prototypes are interactive demos of a website or a software application. These are often used to gather feedback early in the project lifecycle, before the project goes into the final stage of development.
Read moreALL ARTICLES
Contribution
We are happy you want to contribute to DXKB. Please choose your preferred way